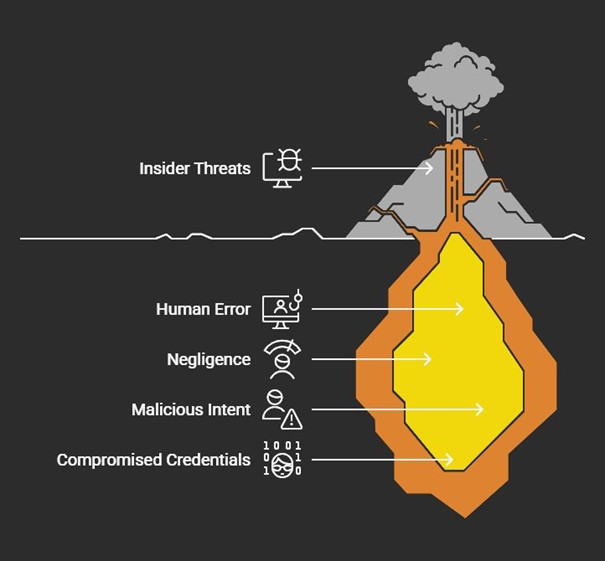
Insider Threats: The Hidden Danger in OT Security
When we think of cybersecurity threats, the image that often comes to mind is that of external attackers—faceless hackers exploiting vulnerabilities from a distance. But in the realm of Operational Technology (OT), one of the most significant and overlooked risks comes from within the organization itself: insider threats.
According to Cybersecurity Insiders, the number of insider attacks, from 2019 to 2024, has increased from 66% of organizations to 76%. (New Report Reveals Insider Threat Trends, Challenges, and Solutions - Cybersecurity Insiders ) Underscoring the need for heightened awareness and mitigation strategies. Whether intentional or accidental, insider threats can be devastating to industrial control systems, manufacturing environments, and critical infrastructure.
Understanding the Different Types of Insider Threats
Insider threats are not one-size-fits-all. They stem from various behaviours and circumstances, each carrying its own level of risk and potential impact:
- Unintentional Actions
Employees may inadvertently compromise OT systems by:
- Clicking on phishing emails that download malware.
- Using weak or reused passwords across systems.
- Accessing OT networks from unsecured personal devices.
These actions, while not malicious, can open doors to external attackers.
- Negligent Behavior
Common examples include:
- Plugging in unauthorized USB drives.
- Connecting unknown or unvetted devices to industrial networks.
- Failing to follow established cybersecurity protocols.
Negligence can introduce malware, trigger vulnerabilities, and increase the attack surface across OT systems.
- Malicious Intent
Disgruntled employees or contractors with privileged access can:
- Tamper with control systems.
- Exfiltrate sensitive data.
- Deliberately sabotage operations or equipment.
These individuals exploit trust and access to cause harm, often in ways that are difficult to detect until it’s too late.
- Compromised Credentials
Even trustworthy team members can become vectors for cyberattacks if:
- Their login credentials are stolen through phishing or malware.
- They are coerced or blackmailed into facilitating unauthorized access.
- Remote access tools are exploited by threat actors.
A compromised user can unknowingly provide a backdoor into otherwise well-protected systems.
Why Insider Threats Are Especially Dangerous in OT Environments
Operational Technology environments present unique vulnerabilities that make insider threats particularly dangerous:
- Operational Disruption: A compromised system can halt manufacturing lines or critical services.
- System Failures: Unauthorized changes to control systems can cause downtime, production errors, or mechanical failures.
- Safety Hazards: In industries like energy, utilities, or transportation, tampering with OT systems can pose life-threatening risks.
- Regulatory and Financial Fallout: Data breaches and system outages may result in hefty fines, legal action, and long-term reputational damage.
Insider threats are not just an IT issue—they’re a strategic business risk that can affect every facet of operations, from safety and productivity to compliance and customer trust.
Building an Insider Threat Defense Strategy
Protecting against insider threats requires a multi-layered, proactive approach that combines people, processes, and technology:
- Implement Role-Based Access Controls: Ensure employees only have access to systems necessary for their roles.
- Monitor User Behavior: Use anomaly detection tools to flag unusual or unauthorized activity in real time.
- Regularly Update Training Programs: Educate employees on recognizing phishing attempts, secure password practices, and OT-specific risks.
- Strengthen Physical Security: Limit access to critical OT systems and equipment.
- Establish a Culture of Security Awareness: Encourage open reporting of suspicious activities and reward responsible behavior.
Final Thought: Awareness Is the First Line of Defense
The most advanced cybersecurity tools can be rendered ineffective if insider threats go unrecognized. By acknowledging and addressing these risks, organizations can protect not only their systems but also their people, processes, and long-term viability.
At Defend-OT, we advocate for a proactive approach to insider threat mitigation—one that bridges the gap between IT and OT security while fostering a culture of vigilance and accountability.
 .
.